For decades, the industry has relied on passwords to prove user identity and ensure security across various domains. In payments, as merchants face increasing pressure to comply with evolving regulations while minimizing customer friction, authentication has become a central area of focus. Diverse approaches are emerging, shaped by varying regulatory demands, consumer expectations, and rapid advancements in technology. This movement goes beyond mere compliance — merchants today aim not only to safeguard against sophisticated fraud but also to build user trust and streamline payment experiences.
Regulation plays a critical role in this transformation. A framework like the Payment Services Directive 2 (PSD2) in Europe has set new benchmarks for transparency, security, and consumer protection. It has inspired similar approaches in other regions, and even in markets with less prescriptive regulation, industry players are adopting PSD2-aligned practices to improve authentication and mitigate fraud. As global payment ecosystems mature, the need for harmonized standards and intelligent authentication strategies has never been greater.
The past year has seen a surge of innovation, particularly from global card networks, aiming to balance security with usability in an increasingly digital-first world. A new generation of authentication methods is taking shape. Passkeys and delegated authentication now enable merchants to verify users directly within their apps, while liability is assumed by the Issuer. Secure Payment Confirmation (SPC) uses WebAuthn and issuer cryptography to deliver instant, browser-native approvals. Click to Pay with passkey support merges network tokenisation, vaulted cards, and device-based biometrics, eliminating the need for manual entry. Issuer-led offerings like Paze Checkout further compress the time between authentication and payment. These methods not only reduce friction but also make authentication more context-aware, secure, and aligned with user behavior across devices.
Before we dive deeper into these trends, let’s first understand what we mean by payment authentication and how frameworks like 3-D Secure and Strong Customer Authentication (SCA) power this critical layer of the payment stack.
What is Payment Authentication?
Payment authentication is the process of confirming that a customer is who they claim to be when making an online purchase. It involves verifying the customer's identity to ensure they are authorized to use the payment method they are providing. This process helps prevent fraudsters from using stolen payment information to make unauthorized purchases.
One of the most widely recognized standards for payment authentication is 3D Secure, it is the primary protocol for complying with Strong Customer Authentication (SCA) requirements under PSD2. PSD2, the revised Payments Service Directive, is a regulatory framework by the European Union that dictates common guidelines for payment service providers in the European Economic Area (EEA).
Before moving ahead, let’s first understand what Strong Customer Authentication is -
What is Strong Customer Authentication (SCA)
Strong Customer Authentication (SCA) is a requirement under the European Union's Revised Payment Services Directive (PSD2). Its main goal is to make electronic payments more secure by adding extra layers of verification. Essentially, it mandates that customers must prove their identity using at least two different authentication factors before a payment can be processed.
SCA mandates that customers confirm their identity using at least two of the following three factors:
- What you have: This could be a device like a smartphone or a hardware token.
- Who you are: This refers to biometric identifiers like fingerprints or facial recognition.
- What you know: This includes passwords, PINs, or answers to security questions.
The role of 3DS as an SCA Enabler
3D Secure (3DS) is a widely adopted protocol that enables Strong Customer Authentication (SCA) for card-not-present transactions under PSD2. It adds an extra layer of security by requiring the cardholder to verify their identity with the issuer, often through biometrics, OTPs, or app-based approval, before completing an online purchase.
Payment Authentication Methods under 3DS
These are the specific ways the cardholder's identity is verified, leveraging the "two out of three" SCA factors:
One-Time Passcodes (OTPs): Codes sent to the cardholder's registered mobile phone via SMS or generated by an authenticator app (possession).
Biometric Authentication: Fingerprint scanning, facial recognition, or voice recognition (inherence), often integrated within banking apps.
Static Passwords/PINs: While less emphasized in newer versions due to security concerns, they can still be a knowledge factor in some implementations.
Knowledge-Based Authentication (KBA): Security questions (knowledge), though their use is also decreasing due to security weaknesses.
Push Notifications: Approval requests sent to the cardholder's banking app (possession), often combined with biometric authentication within the app (inherence).
Hardware Tokens: Physical devices that generate time-based codes (possession).
Security checks beyond 3DS during payment authentication flow
Address Verification System (AVS)
For merchants, Address Verification System (AVS) acts as a security measure to fight credit card fraud. Essentially, AVS checks if the billing address a customer provides during a purchase matches the address the card issuer has on file for that account.
Here's how it works: When a merchant performs an AVS check, their payment gateway sends the numerical parts of the customer's billing address (like the street number and postal code) along with the card details to the customer's issuing bank through payment networks like Visa or Mastercard. The issuing bank then compares these numbers to the address they have recorded for that card and sends back an AVS response code to the merchant. The merchant uses this code, along with other fraud prevention methods, to decide whether to approve or decline the purchase.
AVS adds a layer of security by confirming the knowledge of information associated with the legitimate account holder. AVS makes it significantly harder for fraudsters to complete a transaction which helps merchants to reduce the number of fraudulent transactions that would later result in chargebacks.
However, AVS can sometimes lead to false declines. For instance, if someone uses their work address for a purchase, the AVS might flag it as a mismatch. Additionally, AVS is less effective in areas without consistent address formats. A major limitation is that standard AVS usually only verifies the numerical parts of the address, not the street name, city, or state.
Card verification value (CVV)
The Card Verification Value (CVV), a three- or four-digit security code printed on credit and debit cards (usually on the back for Visa and Mastercard, and on the front for American Express), is a key feature in reducing fraud for transactions where the physical card isn't present (CNP).
When a customer makes an online purchase, they're asked to enter CVV along with other card details. The payment gateway then securely sends this information through payment networks like Visa and Mastercard to the issuing bank. The issuing bank runs a cryptographic check on the CVV and sends back a verification code along with its decision to approve or decline the transaction.
CVV serves as a proxy for proving physical card possession at the time of the CNP transaction. This makes it harder for fraudsters who might have stolen the card number and expiry date (from a data breach, for example) from using a card. Since CVVs are not permitted to be stored by merchants, PSPs, or networks under PCI DSS guidelines, they are typically not leaked in data breaches, which further strengthens their role as a last-mile verification tool. Ultimately, this helps merchants reduce the number of chargebacks filed by legitimate cardholders.
Geolocation
It’s a process of determining the geographic location of the electronic device (like a smartphone, computer, or tablet) being used to initiate a payment transaction using the IP address. It is a risk assessment factor to help verify the legitimacy of the transaction and prevent fraud. It aims to check if the transaction is originating from a location consistent with the legitimate cardholder's known patterns or profile
When a customer initiates a transaction, their transaction location is compared against various data points like billing address, shipping address, historical user behaviour, etc. A transaction is flagged when there are anomalies like Impossible Travel or High-Risk Geographies. A transaction flagged as high risk might require a strong authentication such as a 3D secure payment authentication.
Geolocation helps in enhancing the fraud detection by adding a valuable context to transactions, enabling more accurate risk scoring. This helps merchants in potentially reducing the amount of chargebacks.
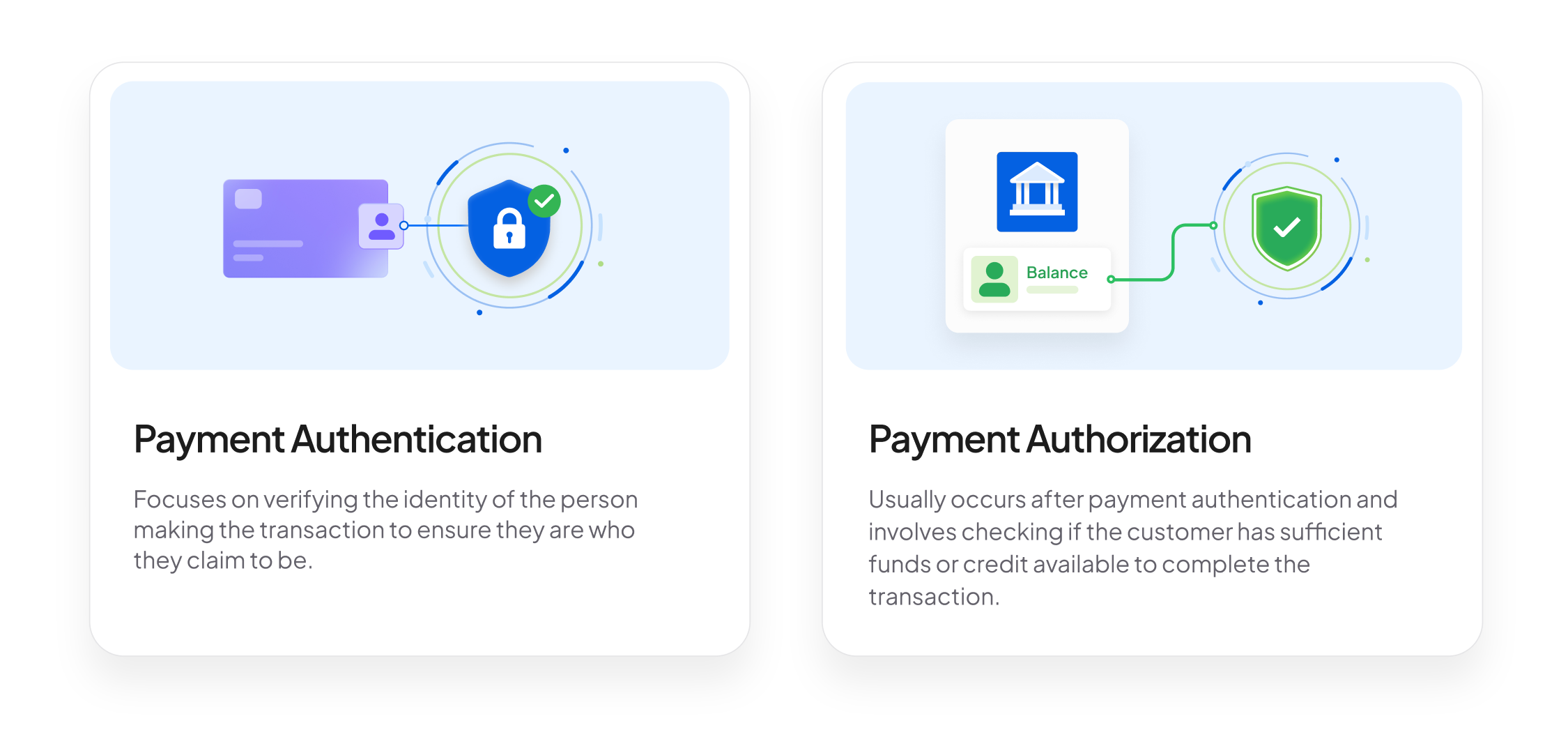
How is Payment Authentication different from Payment Authorization
While the terms "payment authentication" and "payment authorization" are often used interchangeably, they represent distinct processes in a payment transaction:
Payment Authentication: Focuses on verifying the identity of the person making the transaction to ensure they are who they claim to be.
Payment Authorization: Usually occurs after payment authentication and involves checking if the customer has sufficient funds or credit available to complete the transaction.
If payment authentication fails, the transaction will not proceed to the authorization stage, and the payment will be declined. The customer may need to verify their identity or provide additional information to retry the payment.
Both processes are essential for secure online transactions. Authentication prevents unauthorized payments, while authorization ensures that merchants receive payments for completed orders.
Industry-Specific Authentication Challenges
Despite significant innovation, many merchants still face core challenges in executing a consistent and effective authentication strategy.
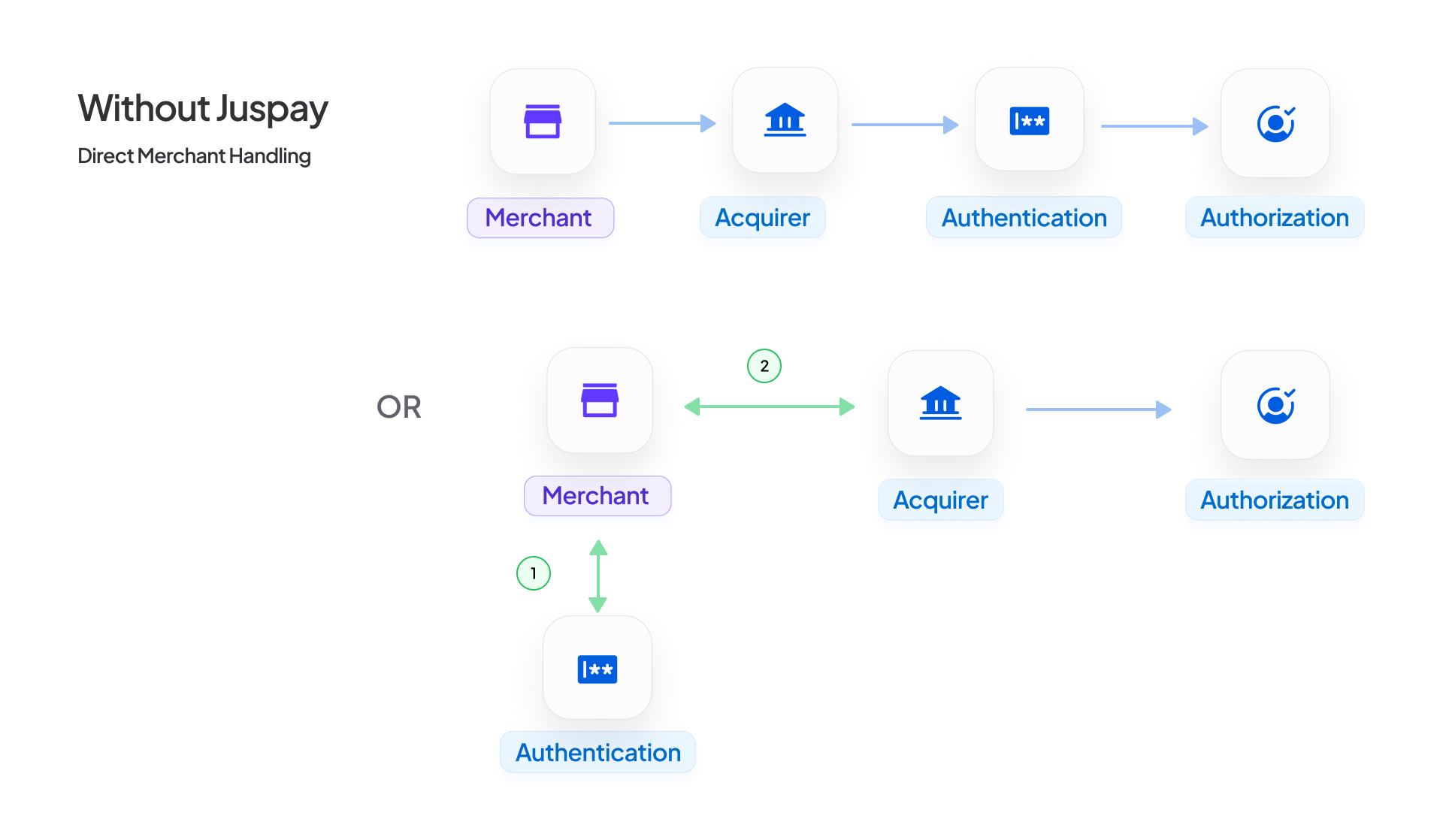
Limited visibility into authentication outcomes is a common issue. Most gateway dashboards focus on authorisation data, which makes it difficult to determine whether a transaction failed due to authentication or funding. Without this clarity, merchants struggle to pinpoint friction points or optimise conversion rates.
Control over authentication strategy is often restricted. Many PSPs provide minimal flexibility, leaving merchants unable to manage exemptions, configure 3-D Secure logic, or route transactions using newer methods such as passkeys or delegated authentication.
Regional inconsistencies further complicate execution. In the United States, 3-D Secure is often viewed as intrusive by both customers and issuers. In contrast, issuers in the European Economic Area treat it as a standard requirement. Even within the EEA, exemption approval rates can vary significantly by country and issuer.
Compliance requirements continue to evolve. For instance, no-3DS transactions are disallowed in the EEA, while passkey-based flows are not yet permitted in markets like India. Each version of the 3-D Secure protocol introduces new data fields and user experience expectations, requiring ongoing updates to merchant implementations.
The pace of innovation is accelerating. Technologies such as Secure Payment Confirmation, network passkeys, and Click to Pay are gaining traction, but adopting them requires merchants to upgrade backend workflows and front-end integrations.
These challenges are especially pronounced in high-risk and mobile-first industries. For example, airlines report that nearly four percent of bookings are cancelled due to suspected fraud. Meanwhile, in mobile commerce, cart abandonment rates can exceed fifty percent when authentication experiences involve delays such as late-arriving OTPs. In such scenarios, rigid and generic authentication flows not only impact conversion but also damage user trust.
Optimize Payment Authentication with Juspay
Juspay has been at the forefront of solving payments ops. for over 12+ years providing enterprise-grade products, solutions and support . We aim at unifying complex, diverse & innovative payment ecosystems and making payments seamless for the end users.
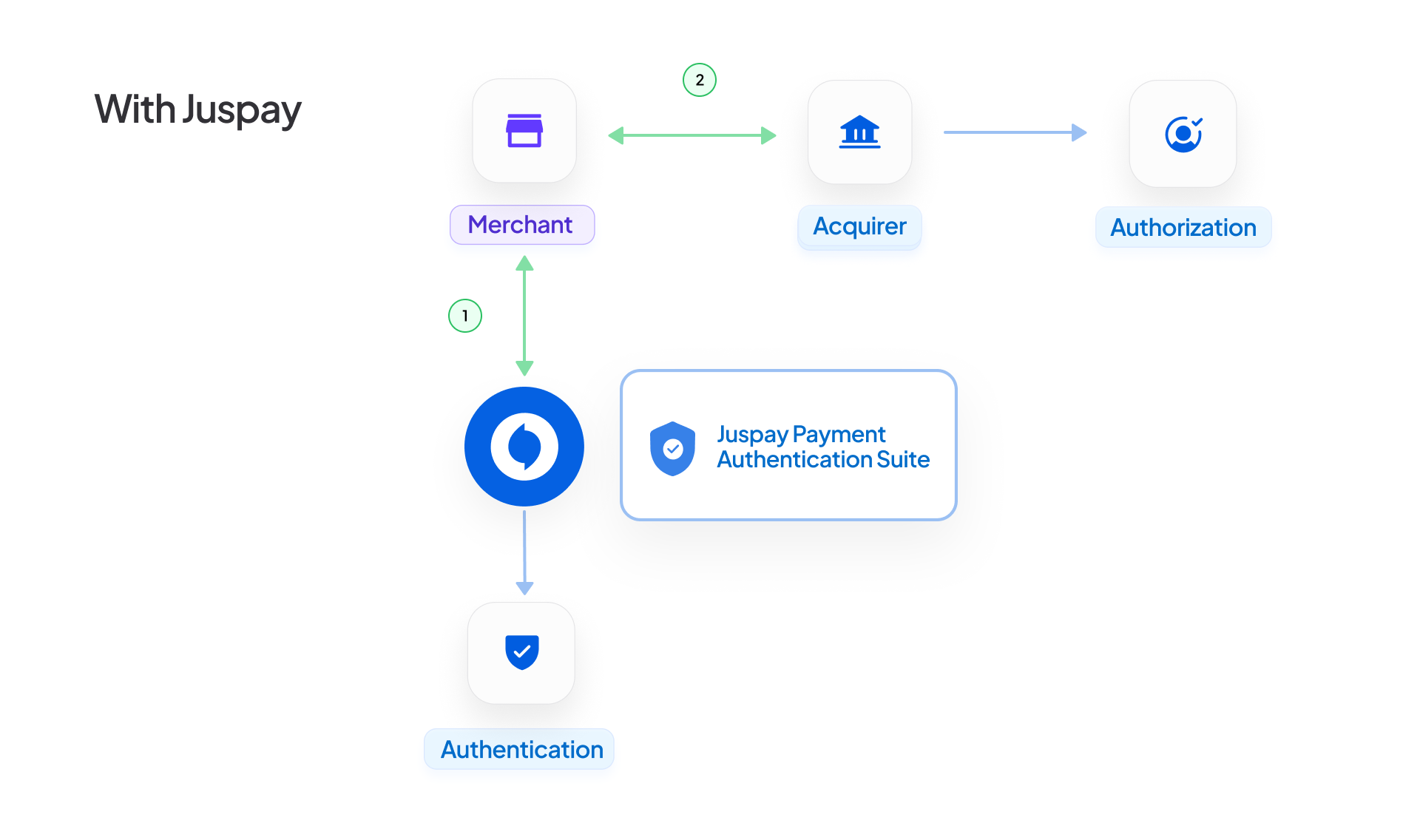
The Juspay Authentication suite is a modular, standalone service that helps merchants gain visibility into authentication performance, ensure compliance, improve user experience, and stay future-ready - all with minimal technical efforts. Juspay offers a unified authentication SDK/API for any authentication mode. It helps merchants manage all their 3DS servers under one integration.
Benefits of Juspay’s Payment Authentication Suite
1. Modular Service - Merchants do not need to overhaul their existing payment stack. Juspay’s authentication suite can be used only for payment authentication, and even selectively for specific features or products.
2. Easy Integration - Juspay’s payment authentication suite offers client SDKs in multiple languages and native authentication SDKs to handle frontend operations smoothly with minimal technical efforts.
3. Payment Service Provider(PSP) and Authentication Provider Agnostic - Juspay’s payment authentication suite works independently of PSPs or authentication providers. Authentication and authorization are decoupled, and any PSP can use the authentication response given by the authentication service for authorization.
4. Future-Proof Architecture - The SDK and APIs are designed to support future product integrations. With a single integration, merchants can add new features with no code changes - just simple dashboard configurations. Juspay’s payment authentication suite can handle authentication with external providers, acquirers, card network and issuer products.

5. Out-of-the-Box Compliance - Juspay’s payment authentication suite ensures global compliance by adapting requests to meet specific market regulations. Merchants can send the same request across markets, and Juspay will handle the compliance logic in the background.
6. Granular Control - Merchants have full control over how payment authentication is executed, within the boundaries of regulatory compliance. Juspay’s payment authentication suite provides multiple levers to the merchants to control the authentication behaviour of the transaction. This allows merchants to implement their own strategy safely.
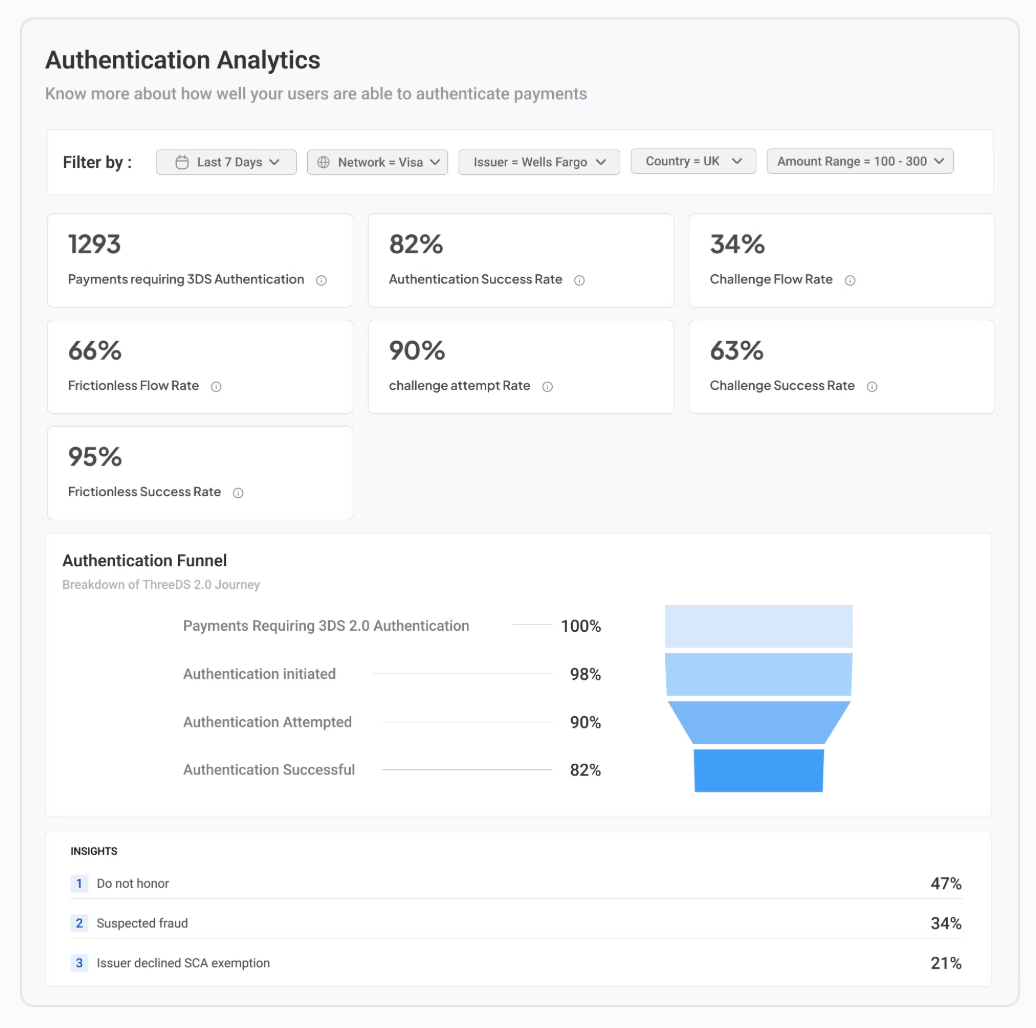
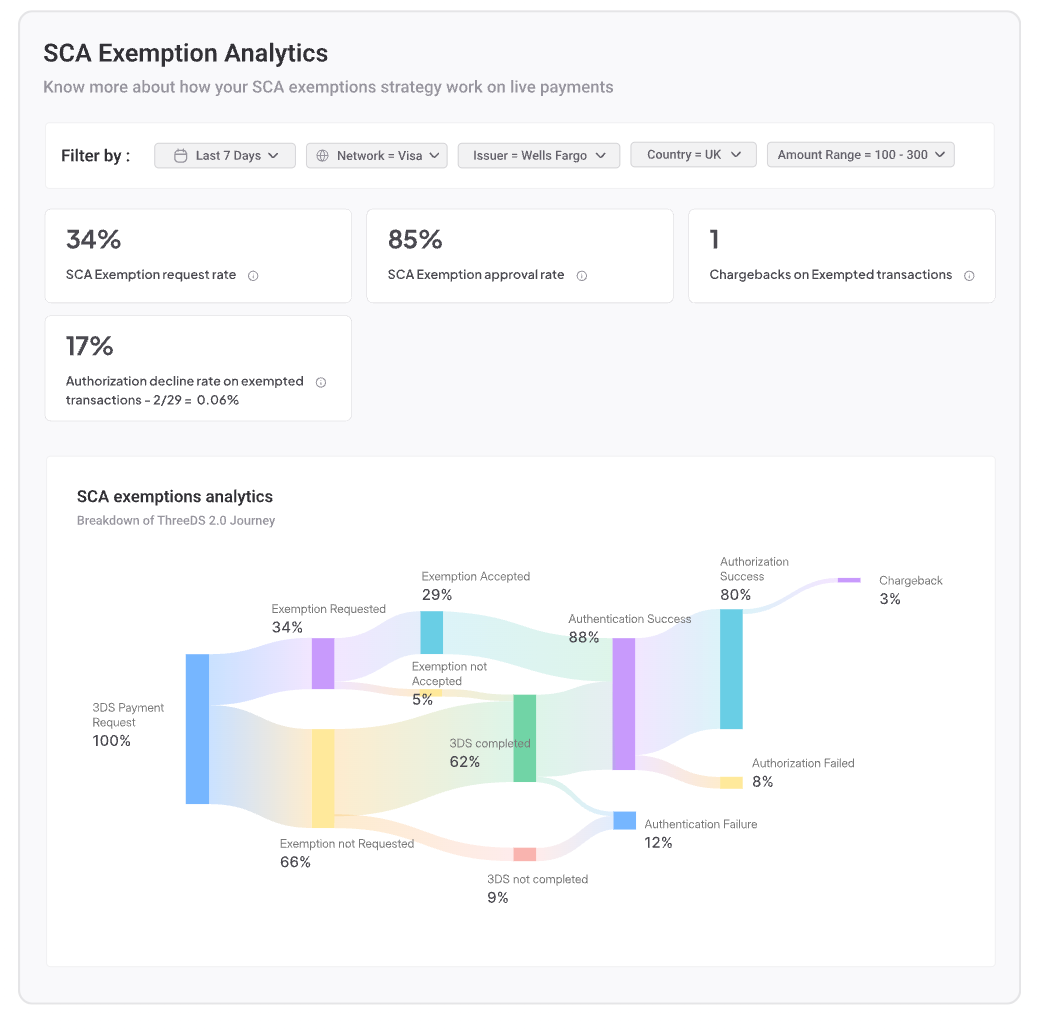
7. Rich Data and Analytics - Juspay’s payment authentication suite offers rich non-sensitive authentication data to merchants, enabling them to gain insights into their authentication flows. An advanced analytics dashboard provides merchants with data across dimensions like market, issuer, network, and user segments. This visibility helps merchants fine-tune strategies and improve conversion rates.
8. Customizable UI - Juspay’s payment authentication suite offers flexible UI customization options, allowing merchants to seamlessly align the checkout experience with their app’s look and feel. From theme and background color to font and button styles, the SDK makes it easy to blend the authentication UI into the overall user interface.
Conclusion
As payment authentication continues to evolve, merchants need a solution that’s not only compliant and secure but also flexible and data-driven.
Investing in the right authentication strategy is no longer optional; it is essential for conversion and for staying ahead of fast-moving standards such as passkeys and Secure Payment Confirmation.
Juspay’s payment authentication suite offers just that - empowering merchants with visibility, control, and scalability. In an era where seamless payments drive conversion and loyalty, investing in the right payment authentication strategy is no longer optional - it’s essential.